It is predicted that groups that were responsible for cyber-attacks on South Korean financial businesses and broadcasting companies on the 20th of March of 2013 are continuing to hack into South Korea’s major facilities. It seems that starting from last year until this year, they have been aggravating cyber confusions by hacking into South Korea’s energy, transportation, communication, broadcasting, IT businesses, financial businesses, and government for more than a year.
Ahnlab’s (CEO Kwon Chi Joong) Security Correspondence Center had revealed about ‘Black Mine Operation’ that was responsible for attacking South Korea’s many organizations and businesses by using same type of harmful codes from May of 2014 to July of 2015.
Harmful codes that corresponding hacking groups had used are similar to that of computer network confusion on the 20th of March of 2013 and same as certain IPs that were accessed during cyber-attack on the 25th of June.
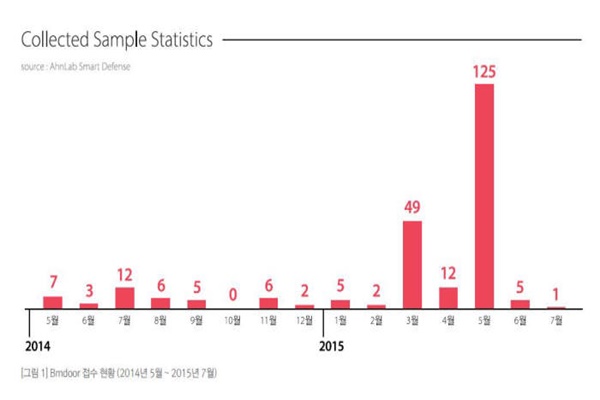
“Group that is responsible for Black Mine Operation was being active until last May and had fallen back a little after June.” said Ahnlab. “However we are paying careful attention as it is possible that they are preparing for new cyber-attacks or actually being active using new harmful codes.” added Ahnlab. Assailants also had hacked into South Korean websites from July of 2014 to March of 2015 and spread harmful codes to computers that were belonged to regular people.
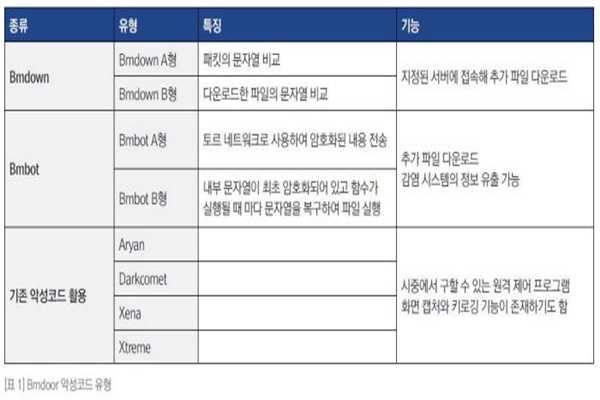
Harmful code that was used for Black Mine Operation is ‘Bmdoor’ and more than 240 of it was found until July of this year. Gathering of corresponding harmful code’s samples from March to May had increased rapidly. Assailants had distributed Bmdoor harmful code to targeted businesses and organizations by disguising it as a file related to work or a PowerPoint file for graduation album or an invitation to alumni association. Although harmful codes become active as soon as PowerPoint file is opened, it is hard for a user to recognize that his or her computer is infected.
Bmdoor gathers infected information about system and is ran by receiving variety of commands as it communicates with C&C (Command & Control) server. Although Bmdoor looks like a normal EXE file, harmful code that is hidden is actually executed from memory because end of a file is encrypted. Its characteristic is that encrypted area starts with a character string of ‘BM’ and it has a function that allows it to bypass an analyst and an automatic diagnostic system.
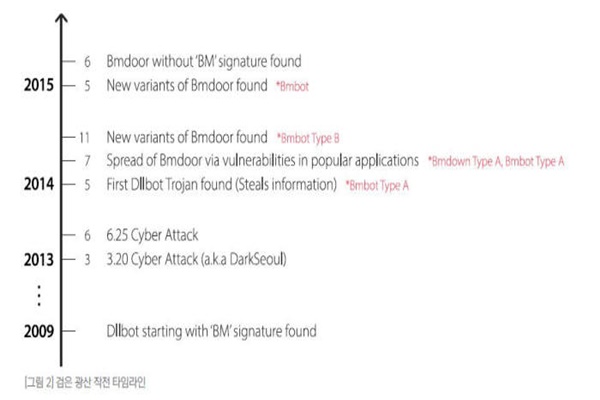
Ahnlab had found Black Mine Operation’s 4 circumstances that correspond to a group that was responsible for computer network confusion on the 20th of March. First of all, many kinds of related harmful codes that include a character string of BM were found from computer network confusion on the 20th of March. Bmdoor that was found in July of 2014 was a modified code that was almost similar to a harmful code from the 20th of March. There is a high possibility that only manufacturers have corresponding harmful codes since they were not found in anywhere else, and even though it is not done by a same group, we can deduce that it was done by a group that works with a group that was responsible for computer network confusion on the 20th of March.
Assailants had used South Korean programs’ weaknesses when they were distributing modified Bmdoor on the 7th of July of 2014, and it is a very similar tactic that was used during computer network confusion on the 20th of March. Modified address and communication address of modified Bmdoor that was distributed on the 7th of July of 2014 have some similarities to that of distributed domain and accessed address of harmful codes that were used during cyber-attacks on the 25th of June of 2013.
“There are definitely groups that are continuously attacking South Korea’s major organizations and businesses in past 10 years.” said an analytical team from Ahnlab. “Major organizations and businesses need to strengthen capabilities of analyzing files that are introduced inside of businesses and strengthen their cooperation with security businesses and relevant organizations.”
Staff Reporter Kim, Insoon | insoon@etnews.com