Chinese hacking, which cannot be deleted once a phone is infected and totally takes control of an Android phone by disguising itself as a popular Android app, is found. South Korea is also a target from this hacking.
FireEye Korea (CEO Chun Soo Hong) made an announcement that it detected two cares of hacking attacks that were presumed to be from Chinese businesses on Android phones. First attack used a method that uses harmful adware to invade into a user’s Android phone and seizing control of it. FireEye believes that Chinese mobile application advertisement company called NGE Mobi/Xinyinhe is behind this attack.
A person or a group that is behind this attack instilled a harmful code into a popular application and distributed it. If a user downloads this harmful app from his or her Smartphone, a harmful code invades Smartphone and sends information from Smartphone to a remote server. Afterwards it receives APK called ‘Root Master’ from a certain URL and does a rooting process in a Smartphone. After it receives a right to root, it implements shell script called ‘rsh’ and inserts root backdoor. When all these processes take place, this harmful app remains in a Smartphone permanently without being able to be removed.
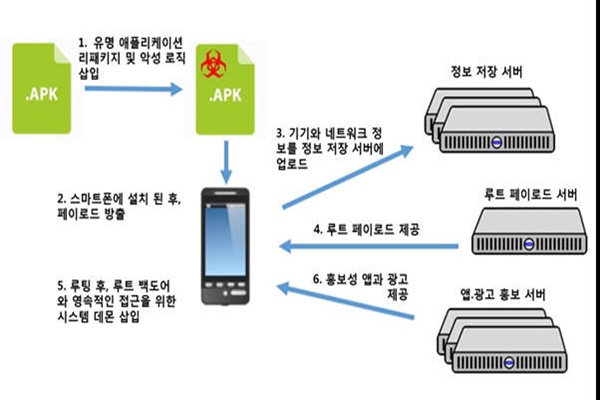
FireEye believes that Chinese mobile application advertisement company called NGE xinyinhe is behind this attack. After analyzing into information about authentication certificate of a server, it was able to find a common came (CN) called ‘ngstream’ from authentication certificate that was used for hacking. ‘ng’ from ‘ngstream’ indicates ‘new galaxy’, which is an English name for ‘xinyinhe’. Organization clause from authentication certificate was also ‘xinyinhe’.
NGE Xinyinhe’s application repacking tool and a key corresponding to server’s authentication certificate that was used for hacking were found, and FireEye believes that those are crucial evidences that a Chinese company is behind this attack. Major channel where hacking incidences occurred is a huge advertisement cooperative network that xinyinhe is part of.
Adware that is invaded into a user’s Smartphone automatically downloads certain application or induces a user to click APK install button. It is known that NGE Xinyinhe has been making its profits by increasing number of downloads of application that it advertises and showing advertisement message continuously.
Harmful adware affects from Android 2.3.4 Version to 5.1.1 Version that includes most of Android versions that are currently used. More than 300 applications such as Amazon, Memory Boost, Clean Master, Flashlight and others were manipulated and affected by harmful codes.
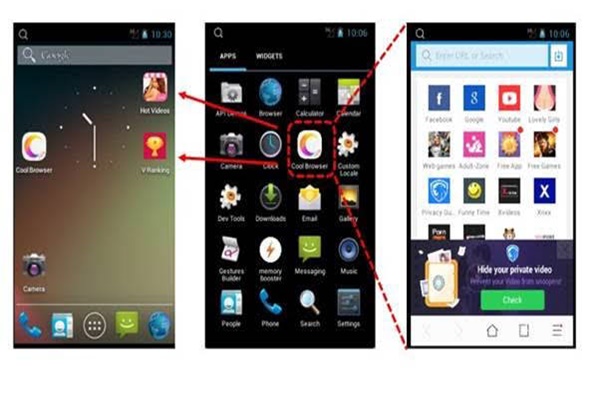
FireEye additionally found an harmful Android adware called ‘Kemoge’ that uses similar method. Just like the other harmful adware, ‘Kemoge’ also disguises itself as a popular application and enters a user’s Smartphone. Once it is inside, it cannot be deleted. From rooting processes from couple incidences, ‘Root Master’ that was used by NGE xinyinhe was used. Both of harmful adware use very similar method.
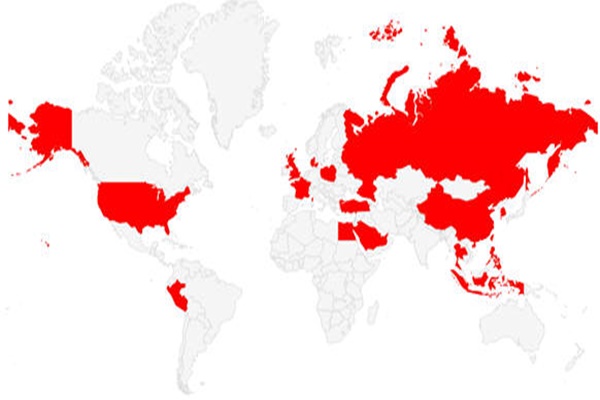
FireEye currently predicts that Chinese person or group is behind this attack based on facts that simplified Chinese characters were found in codes where ‘Kemoge’ incidences occurred and a name of a developer of an application where these incidences occurred was Zhang Long. 20 countries worldwide including South Korea are under areas of influence, and government organizations and huge companies are included as major targets from hacking attacks.
“To protect a mobile equipment from hacking attacks, one needs to refrain from downloading an applications from channels and use the newest Android OS version.” said CEO Chun Soo Hong of FireEye Korea.
Staff Reporter Kim, Insoon | insoon@etnews.com