Hancom’s Hangul, which is a main South Korean software (SW), has become a main passage for hackers. It was shown that Hangul has been used by cyber attacks that mainly target public institutions and schools in South Korea. 123 contaminated Korean documents were found just in 2017.
AhnLab announced that it collected 135 contaminated documents filed from September of 2016 until December of 2017. Hangul is a program that is used most often in South Korea ever since it was released in 1989 and it is also often used by hackers that target South Korean Government, public institutions, and schools. One can avoid attacks from hackers by having the most updated version of Hangul program.
Hackers write emails with information that interests targets that they are going for and induce those targets from opening Hangul files that include malware. Hackers also use addresses where malware can be downloaded instead of directly attaching Hangul files to emails.
19% of these contaminated Hangul files include general information on products, security, notice, and proverbs while. North Korea and virtual currency were responsible for 17% each while finance and resume were responsible for 14% and 8% respectively. After analyzing information of these files, it was seen that hackers targeted workers such as North Korea defectors, activists for human rights in North Korea, researchers, and reporters who have professions related to North Korea and workers related to virtual currency.
Hackers also sent Exe and LNK files that are disguised as Hangul files to their targets. Their attacks that involve Hangul files are divided into weak spots, script, EPS (Encapsulated Post Script), and insertion of individual entity. EPS (75%) was the method that was used most followed by weak spots (14%), insertion of individual entity (7%), and script (4%).
Hackers randomly modified information of documents and use a method where malware is ran irregularly. It is difficult for people to detect attacks that involve weak spots. Number of new weak spots was reduced as Hancom enhanced security of Hangul in 2016. However, hackers still used weak spots from 2016 and attacked people who did not update Hangul security yet.
Hancom Office supports Java script. Hackers write their scripts with malware, and documents that are included with these scripts confirm with users whether or not they want to run such scripts.
EPS is a script that runs Adobe Image. After weak spots that used EPS were found in 2015, contaminated Hangul documents that are written in EPS are still found until today.
“To find weak spots of security, we are participating in Korea Internet & Security Agency’s report reward program (bug bounty) and we are working with private security companies.” said a representative for Hancom. “We are continuing to do our best to enhance security of Hangul and we advise everyone to periodically update security patch of Hangul program to prevent themselves from hackers.”
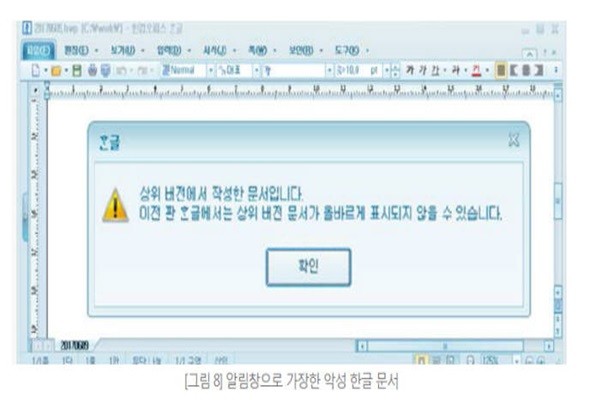
Hackers also use a method of inserting individual entity into Hangul. Although this is not considered as a weak point, they attach codes into documents and induce users to click them. Hackers actually insert malware into Hangul documents. To induce clicks from users, they sent a notification window such as ‘this is a document written from a latest version’.
Malware that is used to contaminate Hangul documents can be divided into ‘downloader’ that downloads other malware and ‘backdoor’ that remotely controls other malware. Downloader is the form that is used the most and it secretly downloads malware from a particular address. Downloader downloads new malware continuously and replaces it with an old malware.
In the past, hackers installed backdoors into PCs by using weak spots of Hangul and ran them. However, malware that is found after September of 2016 is ran from a memory so that it can avoid security solutions. There is also a type of malware that only operates when Hangul is ran.
Staff Reporter Kim, Insoon | insoon@etnews.com